Having explored the concept of service meshes in our previous blog post, we’re now ready to delve deeper into the Istio world, the most widely adopted open-source service mesh platform. While this blog post focuses on establishing a fundamental understanding of Istio’s core features and components, it may serve as a refresher for those already familiar with Istio.
⚡ TL;DR
With Istio, you can connect, protect, control, and monitor a distributed microservice architecture.
Core Features
Istio has five core features that empower the construction of a robust service mesh architecture:
1. Traffic Management
Istio’s straightforward rule configuration and traffic routing give you complete control over the flow of traffic and API calls between your services. It simplifies the setup of essential service-level properties, such as circuit breakers, timeouts, retries, and A/B testing, Canary release, and percentage-based traffic splitting.
This reduces the effort required to configure these critical tasks. With Istio’s traffic visibility and out-of-the-box fault recovery capabilities, you can identify and address problems before they impact your users. This increases the reliability of your calls and improves the overall robustness of your network.
Overview of the traffic management features:
1.1 Gateway
An Istio Gateway acts as a load balancer for incoming traffic as the entry point. It is used to define how traffic from outside the service mesh is routed to specific services or hosts within the mesh.
1.2 Virtual services
A Virtual Service in Istio is used for defining how the traffic within the service mesh is routed. It provides a way to control the traffic between different services based on various criteria.
1.3 Destination Rules
Destination Rules are used to define policies that apply to traffic intended for a specific service within the service mesh. These rules are applied after the traffic has been routed to a particular service by a Virtual Service. Destination Rules are a way to configure and control the behavior of the traffic at the destination service level.
1.4 Fault Injection
Fault injection refers to the intentional introduction of faults or errors into the network communication between services. This is done to simulate and observe how a system behaves under adverse conditions, helping developers and operators to identify and address potential issues proactively.
1.5 Request Timeout
Request Timeout feature allows you to set a maximum duration for how long a request is allowed to take between services in the service mesh. It helps in controlling the maximum time a service is willing to wait for a response from another service. If the response is not received within the specified Request Timeout, the request may be considered as failed, and Istio can take appropriate actions, such as retrying the request or aborting it.
1.6 Retries
Retries allows you to configure how the service mesh should handle failed requests by automatically retrying them. This can be useful for dealing with transient failures, network issues, or temporary unavailability of a service.
1.7 Circuit Breaking
It helps prevent cascading failures in a microservices architecture by controlling the flow of traffic to a service based on its health and the health of its dependencies. The idea is to open the circuit and stop sending requests to a service that is experiencing issues, allowing it time to recover, rather than overwhelming it with more requests that might exacerbate the problem.
1.8 A/B Testing
A/B testing also known as canary testing, is a technique used to release a new version of a service to a subset of users or traffic while still serving the old version to the majority. This allows developers to validate the new version’s performance, reliability, and user satisfaction before rolling it out to the entire user base.
2. Security
Istio takes care of the underlying security infrastructure, allowing developers to focus on building secure applications. It handles authentication, authorization, and encryption of service communications at scale, ensuring secure communication by default. Policies can be applied consistently across different protocols and runtimes with little or no application changes.
Being platform-independent and compatible with Kubernetes (or infrastructure) network policies, Istio offers even greater benefits. It protects both pod-to-pod and service-to-service communications at both the network and application layers, providing a comprehensive security solution for your microservices architecture.
Being platform-independent and compatible with Kubernetes (or infrastructure) network policies, Istio offers even greater benefits. It protects both pod-to-pod and service-to-service communications at both the network and application layers, providing a comprehensive security solution for your microservices architecture.
Overview of the security features:
2.1 Authentication
Istio provides mutual authentication between microservices, so that microservices can be confident that they are communicating with other authorized microservices. This is done through the use of Istio Citadel, which is a component of Istio that provides authentication and authorization services.
2.2 Authorization
Istio provides authorization policies that control which microservices are allowed to communicate with each other. This is done through the use of Istio Mixer, which is a component of Istio that collects telemetry data and applies policies to microservices.
2.3 Certificate management
Istio provides a number of features for managing certificates, such as certificate discovery, rotation, and renewal. This is done through the use of Istio Pilot, which is a component of Istio that manages the Envoy proxies in an Istio mesh.
3. Observability
Istio’s powerful tracing, monitoring, and logging capabilities provide you with a comprehensive understanding of your service mesh deployment. With Istio’s monitoring features, you can gain insights into how service performance impacts upstream and downstream processes. Customized dashboards provide a holistic view of service performance and its overall impact on other processes.
Istio’s component handles policy control and telemetry collection. It serves as an abstraction layer, shielding the rest of Istio from the implementation details of individual infrastructure backends.
This provides operators with fine-grained control over all interactions between the mesh and infrastructure backends. These features enable more effective configuration, monitoring, and enforcement of SLOs. Ultimately, this leads to quicker and more efficient problem detection and resolution.
Overview of the observability features:
3.1 Kiali
Kiali is an observability platform for Istio. It provides a GUI and a set of APIs that enable you to monitor, troubleshoot, and manage your Istio mesh.
3.2 Prometheus
Prometheus is a monitoring system that collects and stores time series data. It is used to monitor a wide range of systems, including microservices, infrastructure, and applications.
3.3 Opentelemetry
OpenTelemetry is collection of APIs, SDKs, and tools for observation and provides a standardized way to collect and export telemetry data, such as metrics, logs, and traces. It is designed to work with a variety of vendors and technologies, making it a versatile tool for monitoring and troubleshooting distributed systems.
3.4 Jaeger
Jaeger is a tracing tool that helps you monitor and troubleshoot complex microservices architectures. It provides a comprehensive view of how requests flow through your system, allowing you to identify and resolve performance bottlenecks, communication issues, and other problems.
4. Platform Support
Istio is versatile and adaptable, working seamlessly across various environments, including cloud, on-premises, Kubernetes, and Mesos .
Istio can be deployed on Kubernetes or on Nomad with Consul. It currently supports:
- Deploying services with Kubernetes
- Consul-registered services
- Services running on individual virtual machines
5. Integration and customization
Istio’s extensible policy enforcement component seamlessly integrates with existing solutions for ACLs, logging, monitoring, quotas, and auditing, enabling comprehensive control and visibility across your infrastructure.
Istio Architecture
The Istio service mesh is divided into two planes: the data plane and the control plane.
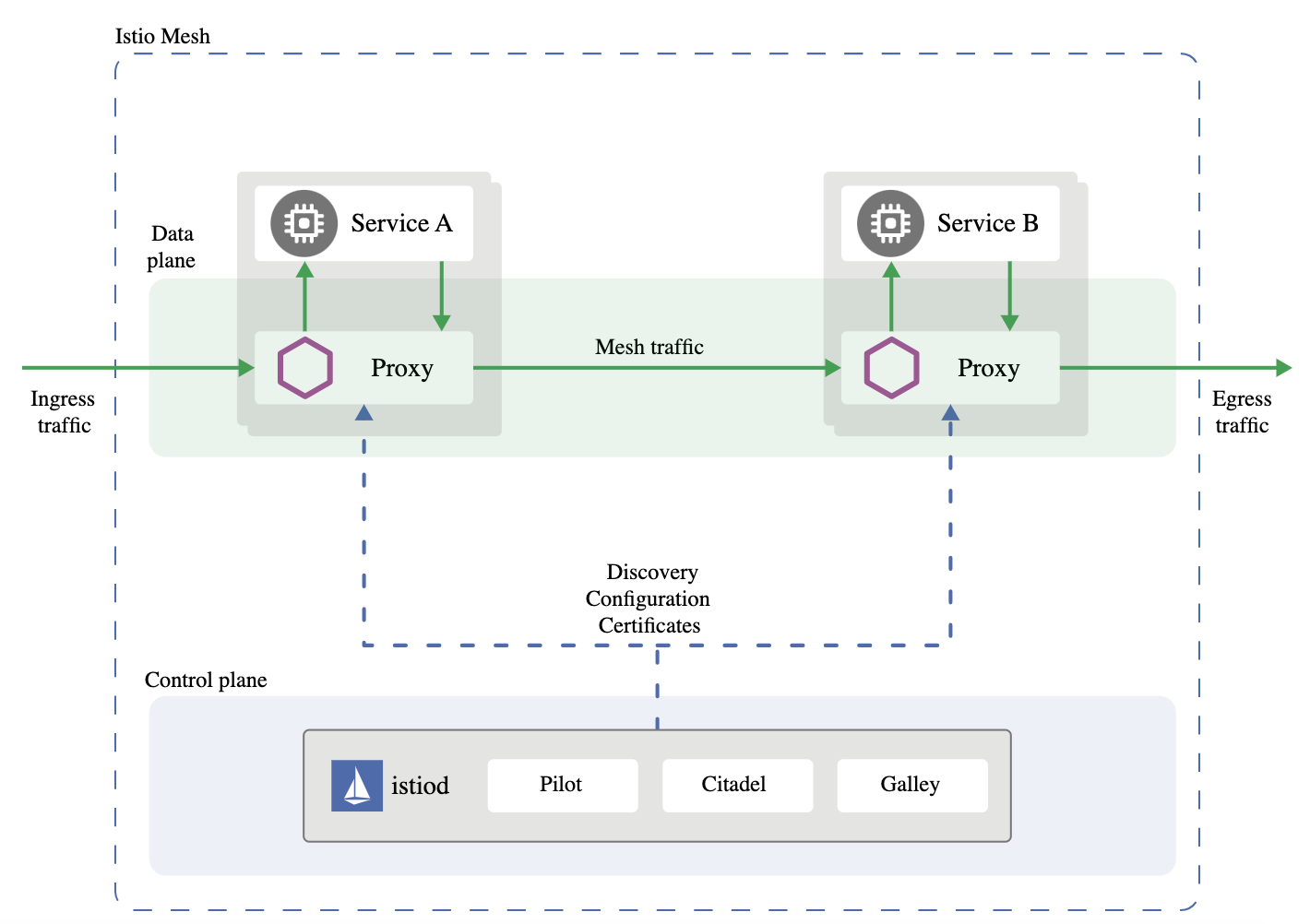
Data Plane
Data plane is made up of a bunch of smart proxies called Envoy. Envoy proxies are deployed alongside your microservices, like little buddies. They handle all the network traffic between your microservices, like routing traffic, making sure your services are following the rules, and collecting telemetry data about how your services are running.
Envoy
Envoy is a powerful C++ proxy that handles all incoming and outgoing traffic for your microservices. It’s like a security guard at the door of your house, but for your microservices. It checks all the traffic to and from your microservices to make sure it’s safe.
Envoy is deployed as a sidecar, which means it runs alongside your microservices in the same Kubernetes pod. This allows Envoy to gather detailed information about the traffic going to and from your microservices.
This information is then sent to a component called Mixer from control plane, which uses it to make policy decisions and send it to the monitoring system. This allows Istio to track how your microservices are performing and make sure they’re following the rules.
Imagine you have a shop, and Envoy is the security guard at the door. It checks all the customers coming in and out of your shop to make sure they’re not stealing anything. Mixer is like the manager of your shop. It uses the information from Envoy to track how the shop is performing and make sure it’s following the rules.
By using a sidecar proxy model, Istio can be easily integrated into existing deployments without requiring any changes to your code. This makes it easy to start using Istio to manage your microservices.
Istio takes advantage of many Envoy features, including:
- Dynamically discovering services (xDS, ESD)
- Balancing traffic (Load balancing)
- Encrypting traffic (mTLS)
- Serving HTTP/2 and gRPC traffic
- Preventing overload (Circuit breakers)
- Checking service health (Health checks)
- Gradually releasing new versions of services (Gradual rollout)
- Simulating errors (Fault injection)
- Enriching data with custom information (Rich injection)
Control Plane
Control plane is the brain of Istio. It’s responsible for managing and configuring the Envoy proxies, and for configuring Mixer, which is a component that applies policies and collects telemetry data.
In other words, the control plane tells the Envoy proxies how to route traffic, and it tells Mixer what policies to enforce and what data to collect.
Imagine you are the CEO of a company, and the Envoy proxies are your sales team. You are the control plane. You tell the sales team where to go and how to sell your product. Mixer is like your finance manager. It collects data about how the sales team is performing and how much money they’re making.
Pilot
The Pilot serves as the traffic manager, responsible for managing the Envoy proxies. Pilot tells the Envoy proxies how to route traffic, and what policies to enforce.
Imagine you are a traffic controller at an airport. The Envoy proxies are like the airplanes, and Pilot is like you. You tell the airplanes where to go and what rules to follow.
The Pilot oversees the Envoy sidecars, instructing them how to route traffic based on various factors. It can perform A/B testing to compare different versions of a service, gradually roll out new versions to minimize disruptions (canary deployment), and implement resiliency features like timeouts, retries, and circuit breakers to handle unexpected situations.
Citadel
Citadel is the security backbone, responsible for managing the identity and security of microservices. It provides a number of features, including:
-
Authentication: Citadel provides mutual authentication between microservices, so that microservices can be confident that they are communicating with other authorized microservices.
-
Authorization: Citadel provides authorization policies that control which microservices are allowed to communicate with each other.
-
Encryption: Citadel provides encryption of traffic between microservices, so that data is protected from unauthorized access.
Imagine that you have a customer who wants to order a product from your warehouse. The customer sends a request to the warehouse’s website. The Citadel proxy intercepts the request and checks to make sure that the customer is authorized to access the warehouse. If the customer is authorized, the proxy forwards the request to the warehouse. The warehouse then sends the product to the customer.
Galley
Galley is the central configuration manager, responsible for validating and distributing configuration to the other components of Istio, such as Pilot and Citadel. This configuration includes things like service definitions, routing rules, and security policies.
Imagine you are a teacher at a school. The other components of Istio are like the students in your class. You are like the school librarian. You make sure that the textbooks and other materials that the students need are correct and then distribute them to the students.
It acts as a middleman, shielding other Istio components from the complexities of retrieving and processing configuration data from underlying platforms like Kubernetes.
Mixer
Mixer is a platform-independent component and acts as a gatekeeper and data collector for the service mesh.
It is responsible for collecting telemetry data from microservices and applying policies to them. Telemetry data includes things like metrics, logs, and traces. Policies are rules that control how microservices can communicate with each other.
Imagine you are the manager of a factory. The microservices are like the workers in your factory. Istio Mixer is like the quality control department. It collects data about how the workers are performing and makes sure that they are following the rules.
Summary
Istio’s innovative architecture and comprehensive feature set have propelled it to the forefront of service mesh solutions. By leveraging Istio, organizations can reap significant benefits in terms of microservices management, security, observability, and traffic management, paving the way for agile and resilient microservices deployments.
Stay tuned for the next blog, where we’ll delve into a comparative analysis of leading service mesh providers, highlighting their strengths and weaknesses to guide your informed decision-making.